
Photo by Dmitry Ratushny on Unsplash
Open-Source Intelligence - An open veil into your life!!
How Open-Source Intelligence (OSINT) can be used to obtain information about you
A picture is worth a thousand words, indeed!!

Imagine that the above picture, from a target, is all we have to 👀👀 into their lives and obtain the following information:
- What is their avatar
- What city they are in
- The SSID of the WAP they connected to
- Their email address
- The site from which we soured their email address
- Their holiday destination
- Their password
Well, it's just a picture !!!
Background Story
The world is now connected, at the click of a button we can chat, video call, etc. Alas, in hindsight we have sacrificed privacy in return for convenience. The concept of abstraction comes to my mind – users are not shown the complicated behind-the-scenes stuff. For example, if you take a picture, there is no need for you to know the whole process of pixel painting to create a digital image. The user can only see the picture and maybe the filename and the date modified after sifting through the file's properties.
Abstraction serves us the time not to be worried about the nitty-gritty and focus on the result, our savior and devil. The pictures we take contain what is called metadata which can be extracted from the picture. Through analyzing the extracted meta-data a researcher/attacker can determine the device used to paint the Kodak moment, the date the picture was taken. Geo-tagging enables us to attach our location (where the picture was taken) to a picture and, alas, this can also be extracted from the meta-data of your image. Meaning anyone who has access to your pictures can determine places you frequent or even your current location as we tend to send pictures tagged “Current what what!!” on social media. How about that? Maybe if the metadata was not hidden due to abstraction we would think twice before posting. Like, “Do I need this information to be in the public domain, my location ?”. For us general users it’s “just a picture”.
The practicality side of this gospel (the gospel according to Tafadzwa Demba) can be Illuminated through a walk-through of Try Hack Me Open Source Intelligence Challenge which the writer successfully aced.
Enter ExifTool
Analyzing the picture with our naked eye: it’s a Windows XP background image. But wait, there is more to the picture than what is visible to the naked eye! Enter ExifTool .
To extract the metadata from the picture the writer used ExifTool, the right tool for the job.
"ExifTool is a platform-independent Perl library plus a command-line application for reading, writing and editing meta information in a wide variety of files".
Using ExifTool To Obtain MetaData
Executing the command in terminal
exiftool WindowsXP.png
resulted in the following output, harvested from meta tags, and voila we now have a flag that will help us dig much deeper into identifying our target. (Owoodflint is our target as shown by the output of the ExifTool command - exiftool WindowsXP.png)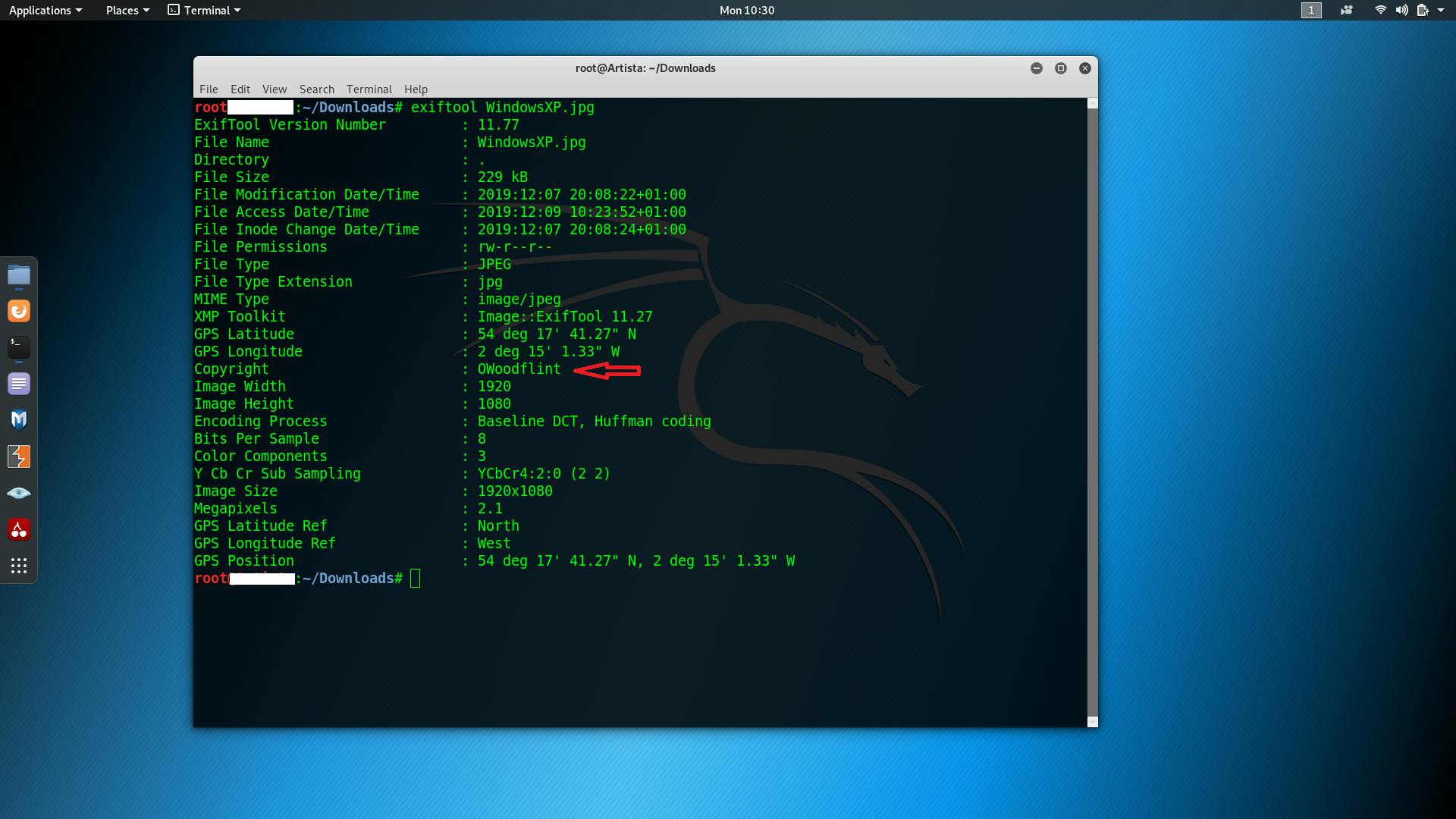
Digging deeper into Owoodflint - thanks to the picture 😿
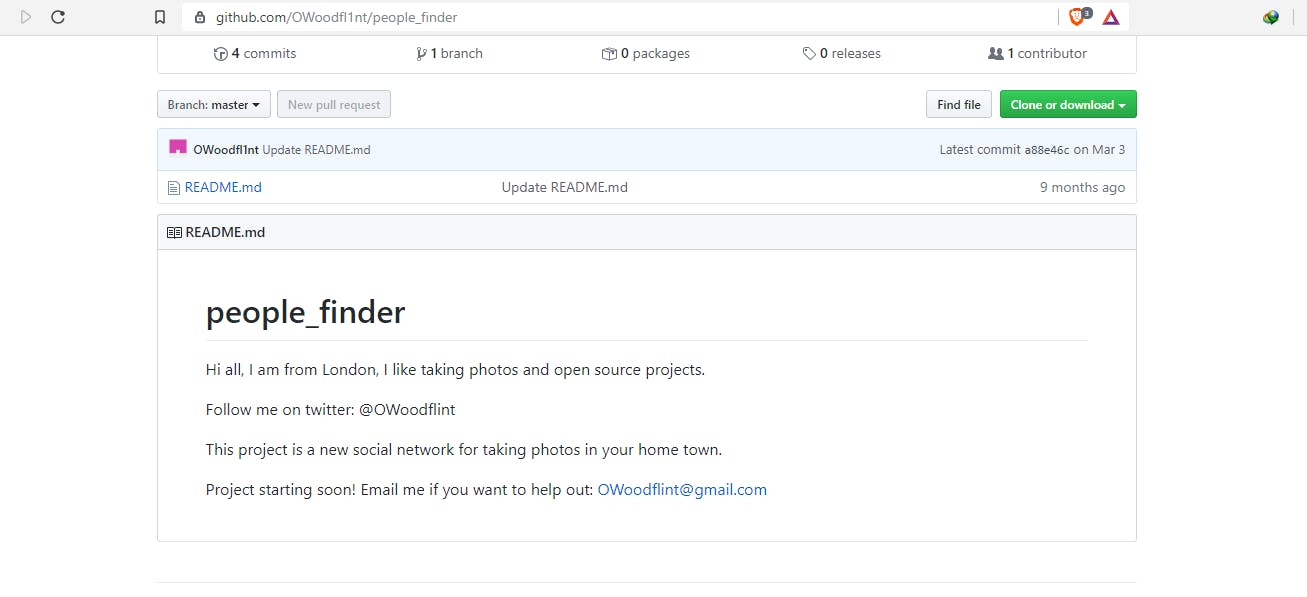
A Google search, Owoodflint, leads us to their twitter account, github page and also their personal blog.
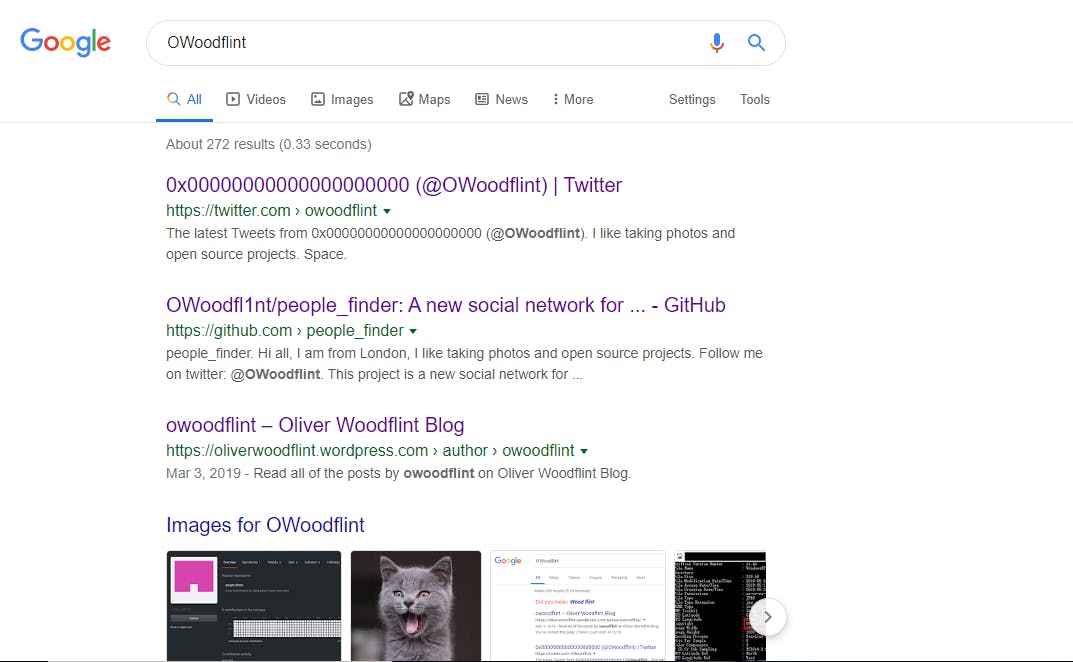
We are heading in the right direction don't you think?
Personal Information From Their Twitter Account
Browsing through the target's Twitter page the writer was able to determine the BSSID of the target as they voluntarily shared it on Twitter. We can’t blame them as most of us are prone to what I call compulsive-voluntary-oversharing.
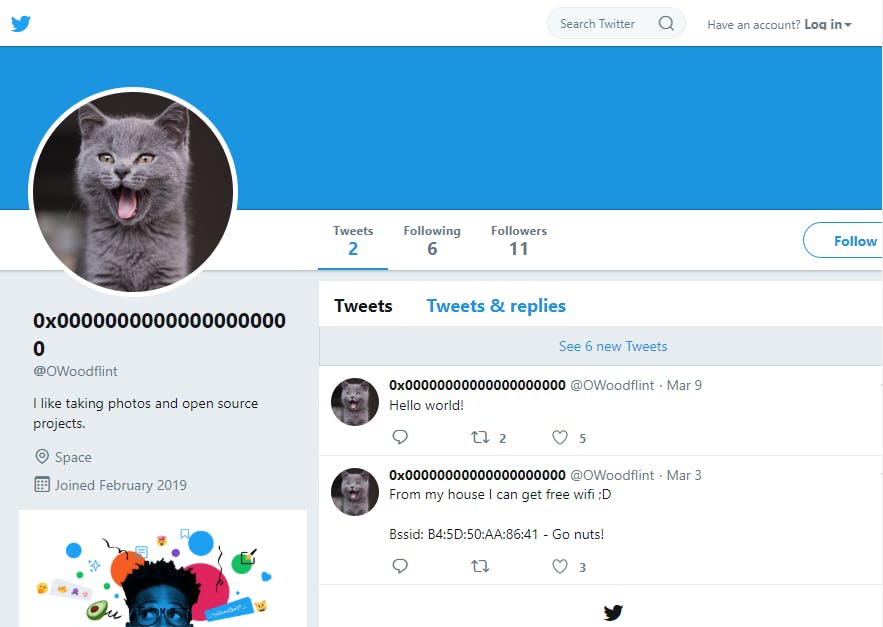
This action led to the writer discovering the target’s home location by entering the BSSID on wiggle.net.
According to Wikipedia - wiggle is a website for collecting information about wireless hotspots around the world, hence the target's city was obtained. (Objective 2, knowing their city, Done!). Objective 1, avatar, is also done.
The target's location basing on BSSID as seen on Wigle
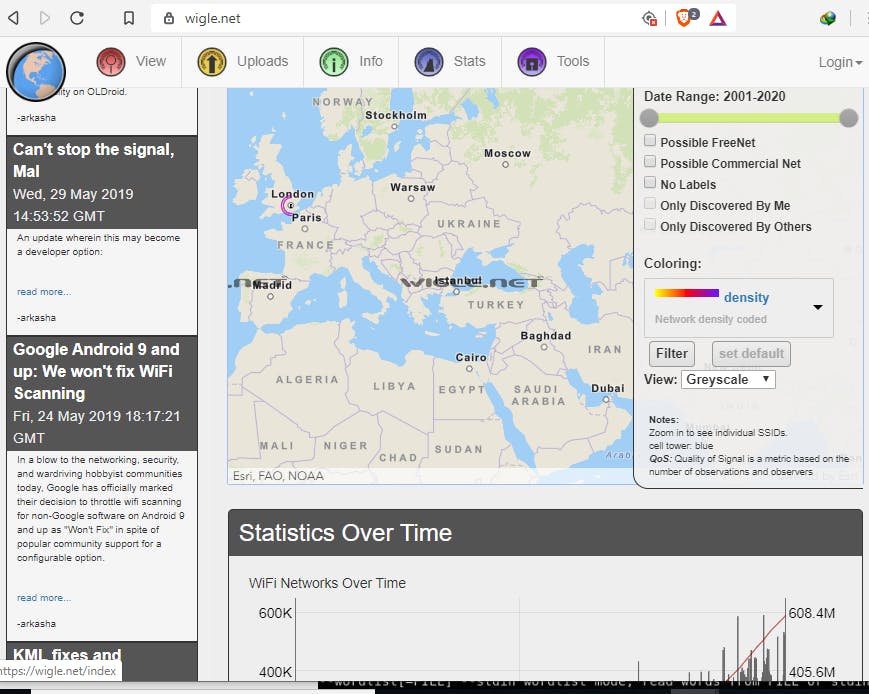
Zoom out if you cannot properly see the Location on the map, the target’s location is indicated by a purple semi-circle. BSSID is simply the MAC address of a wireless access point, used to uniquely identify the wireless access point.
Zooming in on the city on wigle also resulted in the SSID ( the unique name of the wireless access point in simple terms) being identified hence acing Objective 3
Objectives 4, 5 and 6
Owoodflint also volunteered their email address on GitHub hence completing objective 4 (personal email) and objective 5 (site) collectively. Think of all those places you volunteered your email address! Their location is also there on their GitHub hence providing another vector of completing objective 2( city).
On their blog, the target also disclosed that he is on holiday in New York hence acing objective 6 (holiday).
As for Owoodflint's password, I live it up to the reader to hunt for it through Open Source Intelligence. I will be glad to give some pointers in the comment section.
A moment of reflection, shall we?
All these procedures are legal as information has been obtained through Open Source intelligence, and the information is in plain sight. The above scenario hits close to home as it mimics our behavior online. We overshare, we are not aware of what we are actually sharing hence leaving ourselves digitally vulnerable. We care so much about the physical thieves and tend to forget about the peeping tom in the digital realm hence we become digitally-naked.
How can we protect ourselves from Open Source Intelligence(OSINT)?
- Digital brakes – learn what to share, have a boundary. Do not just volunteer information. The target went on to brag about stealing Wi-Fi and went to the extent of publishing the BSSID. How great!
- Device manufacturers can also loosen the abstraction mantra and show the associated information that a user will be sending when they send a file hence they can decide.
- Disable geotagging on mobile phones hence your location cannot be easily determined by extracting metadata from your images or anything your share online be it on WhatsApp, Facebook, etc.… ( make them work for it).
If the above measures do not work why not do it the old-school style? Cut the internet cable or burn your WiFi router and travel 30km to your aunt and show them an old-school photo of your kid taken from a vintage Kodak camera!!!!!🤣🤣🤣🤣🏃🏃
Protect your digital identity. It is your responsibility!
